The "Cyber Breach at Target" case study discusses the password creation policies and practices of various e-commerce websites. It presents steps on how to address the cyber breach and looks into more ways to secure a company's network from threats of the breach and to keep it safe from potential cyber fraud.
Suraj Srinivasan; Lynn S. Paine; Neeraj Goyal
Harvard Business Review (117027-PDF-ENG)
July 07, 2016
Case questions answered:
Case study questions answered in the first solution:
- Compare the personal (user account) password creation policies and practices of any three (but prominent) e-commerce websites and prepare a list of their best practices that would help prevent an incident like the Cyber Breach at Target. What further advice, if any, would you like to give them with respect to user password creation?
- As you reach your office one day, you strongly suspect that your corporate network is under attack.
(a) List the immediate steps you should take as the Chief Technology Officer (CTO).
(b) Can you suggest some ways of prior preparedness by which, whenever such suspicion arises, all corporate IT assets (data, applications, etc.) can be immediately isolated and protected? - Explain the public and private key encryption methods.
Case study questions answered in the second solution:
- What do you think contributed to the cyber breach at Target?
- What was the effect of such a cyber breach?
Not the questions you were looking for? Submit your own questions & get answers.
Cyber Breach at Target Case Answers
You will receive access to two case study solutions! The second is not yet visible in the preview.
Q1. Compare the personal (user account) password creation policies and practices of any three (but prominent) e-commerce websites and prepare a list of their best practices that would help prevent an incident like the Cyber Breach at Target. What further advice, if any, would you like to give them with respect to user password creation?
The following data is about the password creation policies of e-commerce websites such as Amazon, Walmart, Paytm, etc. Included in the following are their best practices, which would help prevent an incident like the Cyber Breach at Target.
a. AMAZON: The password policies of Amazon include the following points
- Amazon always prompts you to change the password from time to time and keep the password private.
- The password should be a minimum of 6 characters, and a maximum of 1024 characters is allowed. However, Amazon prompts us to use at least 8 characters.
- It is suggested that you should not keep the passwords too easy to decipher, such as your own username or sequence numbers, such as 123456. Any personal information about you is also not recommended as a password.
- However, there is no compulsion to use special characters in the password; you can use them to increase the strength of the password.
b. WALMART: Walmart has mentioned the following things that one user should and should not do
- The password string should be of at least 8 letters or numbers
- It is suggested that the password for the Walmart account should be different from other accounts.
- Change your password periodically.
- Give the password only via a secure connection.
- Do not use your mobile number, address, or any common information about you, such as your dog’s name.
- Do not give your password by email
- Do not keep your passwords near your computer
c. PAYTM: The password string in Paytm should consist of a minimum of 5 characters.
- It should have at least one number and one alphabet.
- Also, while accessing the Paytm wallet, the username and password of the account are not the only things needed. There is another layer of the password given by Paytm called a passcode, which is a 4-digit code.
- The 4-digit passcode safeguards the wallet transactions; even if your Paytm account is logged in, you will need to enter the passcode for every transaction.
- Also, while logging in from other devices, Paytm user and password are not sufficient; you will need to enter the OTP, which is sent to the registered mobile number.
Pieces of advice that can be given in user password creation that would help mitigate cyber breaches like the one that happened at Target:
- Do not open too many accounts for the same website or the same app.
- It will be difficult to remember each and every password, so keep track of such passwords in a secure place.
- If you are saving your passwords on a cloud, it is better to save them by coding them in a different way, and only you should know how to decode them.
- Various companies can apply to encode the passwords, such as timestamps. This will enable users to choose the same passwords, but when the system has the password, it will get it with the timestamp of login. In this way, it will be different for every user.
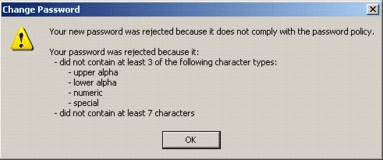
Fig 1: Password creation error
E.g., When password policy is not followed, such pop-ups are shown stating the password policies
Q2. As you reach your office one day, you strongly suspect that your corporate network is under attack.
(a) List the immediate steps you should take as the Chief Technology Officer (CTO).
(b) Can you suggest some ways of prior preparedness to avoid incidents like the Cyber Breach at Target, by which whenever such suspicion arises, all corporate IT assets (data, applications, etc.) can be immediately isolated and protected?
SOLUTION a:
As a CTO, one should take the following immediate steps in response to a cyber attack…
Unlock Case Solution Now!
Get instant access to this case solution with a simple, one-time payment ($24.90).
After purchase:
- You'll be redirected to the full case solution.
- You will receive an access link to the solution via email.
Best decision to get my homework done faster!
Michael
MBA student, Boston
 Best decision to get my homework done faster!
Best decision to get my homework done faster!